Structure of a Secure Operating System
» Table of Contents | » Glossary | » Index |
In the late 1960s, a great deal of research and development was dedicated to the problem of achieving security in multiuser computer systems. Much of the development work involved attempts to find all the things that could go wrong with a system's security and then to correct those flaws one by one. It became apparent to the researchers that this process was ineffective; effective system security could result only from a basic model of the structure of a secure computer system. The reference monitor concept was proposed as such a model and gained wide acceptance.
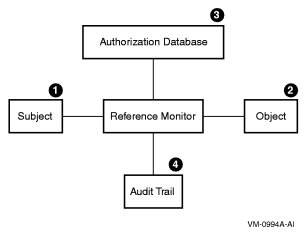
According to the reference monitor concept, a computer system can be depicted in terms of subjects, objects, an authorization database, an audit trail, and a reference monitor, as shown in Figure 2-1 “Reference Monitor”. The reference monitor is the control center that authenticates subjects and implements and enforces the security policy for every access to an object by a subject.
The following table describes the elements shown in Figure 2-1 “Reference Monitor”:
The reference monitor enforces the security policy by authorizing the creation of subjects, by granting subjects access to objects based on the information in a dynamic authorization database, and by recording events, as necessary, in the audit trail. In an ideal system, the reference monitor must meet the following three requirements:
Mediate every attempt by a subject to gain access to an object
Provide a tamperproof database and audit trail that are thoroughly protected from unauthorized observation and modification
Remain a small, simple, and well-structured piece of software so that it is effective in enforcing security requirements
These are the requirements proposed for systems that are secure even against penetration. In such systems, the reference monitor is implemented by a security-related subset, or security kernel, of the operating system.